User Tools
Site Tools
Table of Contents
IPsec
IPSec (Internet Protocol Security) is a collection of protocol extensions for the Internet Protocol (IP). The official information on encryption and authentication of those responsible for IP information and security for secure communication in IP rights such as the Internet.
IPsec strongSwan
strongSwan is an OpenSource IPsec implementation. It was originally based on the discontinued FreeS/WAN project and the X.509 patch that we developed. In order to have a stable IPsec platform to base the extensions of the X.509 capability on, we decided to launch the strongSwan project in 2005. Since then a new IKE daemon has been written in a modern object-oriented coding style so that the current code base does not share code with its ancestor anymore. Initially that daemon only supported IKEv2, while IKEv1 was handled by an extended version of FreeS/WAN's pluto daemon. But because adoption of IKEv2 by other vendors took longer than anticipated support for IKEv1 was added to the new daemon with strongSwan 5.0.0.
strongSwan originally was designed for Linux, but has since been ported to Android, FreeBSD, Mac OS X, Windows and other platforms.
The focus of strongSwan is on
- simplicity of configuration
- strong encryption and authentication methods
- powerful IPsec policies supporting large and complex VPN networks
- modular design with great expandability
[Source|https://www.strongswan.org/about.html]
Our current Strongswan Version - Linux strongSwan U5.5.1/K4.19.43
Tested Compatibility to Third Party Vendors
- Netgear FVL328
- Firebox X10e
- CISCO ASA5505
- CISCO 820
- Virtual/GNS3 Cisco7200
- Sarian XR2110
- Draytek Vigor 2950
- Astaro Firewall
- bintec/funkwerk R1200wu
How to setup IPsec
The following step by step instruction will guide you through a IPsec configuration. So basically IPsec does have two different modes:
Tunnel mode:
- Tunnel mode protects the internal routing information by encrypting the IP header of the original packet. The original packet is encapsulated by a another set of IP headers.
- It is widely implemented in site-to-site VPN scenarios.
- NAT traversal is supported with the tunnel mode.
- Additional headers are added to the packet; so the payload MSS is less.
Transport mode:
- The transport mode encrypts only the payload and ESP trailer; so the IP header of the original packet is not encrypted.
- Unordered List ItemThe IPsec Transport mode is implemented for client-to-site VPN scenarios.
- NAT traversal is not supported with the transport mode.
- MSS is higher, when compared to Tunnel mode, as no additional headers are required.
- The transport mode is usually used when another tunneling protocol (such as GRE, L2TP) is used to first encapsulate the IP data packet, then IPsec is used to protect the GRE/L2TP tunnel packets.
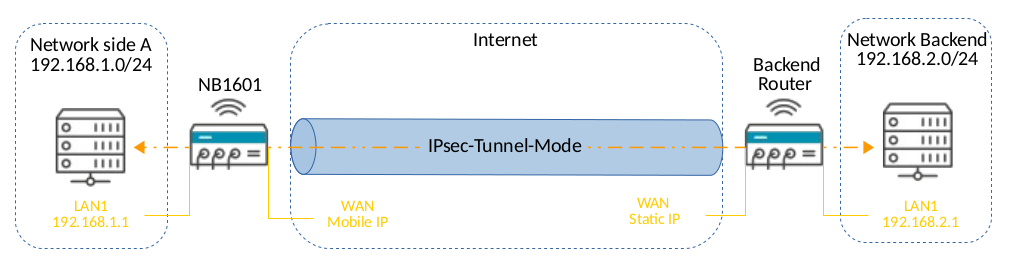
Network setup
For this configuration we will use the most common mode, the tunnel mode. For this example we are using PSK as authentification method.
| SideA | Backend | |||
|---|---|---|---|---|
| Local WAN | Remote WAN - > | < - Remote WAN | Local WAN | |
| 10.10.10.1 | 10.10.10.2 | 10.10.10.1 | 10.10.10.2 | |
| General | Parameter | - | General | Parameter |
| Remote peer address | 10.10.10.2 | Remote peer address | 0.0.0.0 | |
| Dead Peer Detection(DPD) | Parameter | Dead Peer Detection(DPD) | Parameter | |
| Detection cycle | 30 sec | Detection cycle | 30 sec | |
| Failure threshold | 3 | Failure threshold | 3 | |
| Action | hold | Action | hold | |
| Authentication | Parameterc | Authentication | Parameter | |
| Key exchange | IKEv2 | Key exchange | IKEv2 | |
| Authentication type | pre shared key | Authentication type | pre shared key | |
| PSK | “TopSecret01” | PSK | “TopSecret01” | |
| Local ID type | FQDN | Local ID type | FQDN | |
| Local ID | “sideA” | Local ID | “backend” | |
| Peer ID type | FQDN | Peer ID type | FQDN | |
| Peer ID | “backend” | Peer ID | “sideA” | |
| IKE Proposal - Phase1 | Parameter | IKE Proposal - Phase1 | Parameter | |
| Negotiation mode | aggressive | Negotiation mode | aggressive | |
| Encryption algorithm | AES256 | Encryption algorithm | AES256 | |
| Authentication algorithm | SHA256 | Authentication algorithm | SHA256 | |
| Diffie-Hellman group | Group14(modp2048) | Diffie-Hellman group | Group14(modp2048) | |
| Pseudo-random function | undefined | Pseudo-random function | undefined | |
| SA life time | 86400 sec | SA life time | 86400 sec | |
| IPsec Proposal - Phase2 | Parameter | IPsec Proposal - Phase2 | Parameter | |
| Encapsulation mode | Tunnel | Encapsulation mode | Tunnel | |
| IPsec protocol | ESP | IPsec protocol | ESP | |
| Encryption algorithm | AES256 | Encryption algorithm | AES256 | |
| Authentication algorithm | SHA256 | Authentication algorithm | SHA256 | |
| SA life time | 28800 sec | SA life time | 28800 sec | |
| Perfect forward secrecy (PFS) | disable | Perfect forward secrecy (PFS) | disable | |
| Force encapsulation | enable | Force encapsulation | enable | |
| Networks | Parameter | Networks | Parameter | |
| Local network | 192.168.1.0 | Local network | 192.168.2.0 | |
| Local netmask | 24 | Local netmask | 24 | |
| Remote network | 192.168.2.0 | Remote network | 192.168.1.0 | |
| Remote netmask | 24 | Remote netmask | 24 |
All necessary firewall rules for the IPsec functionality will be set automatically, with the enable of the IPsec service.
Server mode
There is also the opportunity to turn units into a IPsec server mode. By setting the remote peer address to 0.0.0.0 you're enable the mode. It basically means the router will accept any IP address with incoming initizalisation content for IPsec communication.
Expert mode
Our Software also can handle customized IPsec configurations. It's compatibility to the tested third party vendors. By simply uploading the IPsec configuration, the VPN communication can be established easily and fast.